
What is an API?
APIs (Application Programming Interfaces) are a way for different software systems to communicate with each other. They allow the frontend (i.e. the part of the application that interacts with the user) to send requests to the backend (i.e. the part of the application that interacts with the database or other external services) and receive responses.
APIs are like the middlemen of the internet. They're the go-betweens that help different websites and apps talk to each other, kind of like that one friend you have who's really good at setting people up on dates.
Just like your matchmaking friend, APIs make sure that the right information gets sent to the right place, so everyone's happy and nobody gets ghosted.
APIs are like the oxygen of the internet. They're everywhere and you don't even realize it. They're the secret sauce that makes all your favorite apps and websites work together seamlessly.
APIs are a fundamental building block of the modern internet, and their presence can be found everywhere from web development to mobile apps, to cloud computing and beyond.
Their widespread use and integration allow for seamless communication and data exchange, and their importance in driving innovation in the software industry cannot be overstated.
Types of API
Public API - Also known as Open API available to developers and other users with minimal restrictions.
Partner API - A partner API, only available to specifically selected and authorized outside developers or API consumers, is a means to facilitate business-to-business activities.
Internal API - An internal or private API is only meant to be used inside the company to link together systems and data. For instance, an internal API may link the payroll and HR systems of a firm.
Composite API - A composite API majority of the time, integrates two or more APIs to create a chain of connected or interdependent activities.
Types of API Protocols
SOAP - Simple Objects Access Protocol
REST - Representational State Transfer
JSON-RPC - JavaScript Object Notation- Remote Procedural Call
gRPC - Google Remote Procedural Call
GraphQL - Graph QL
XML-RPC - Extensible Markup Language Remote Procedural Call
Apache Thrift - Implementation of RPC framework
We will be focussing on Rest and Soap Protocol in this blog.
What is Rest and Soap Protocol
Soap Protocol
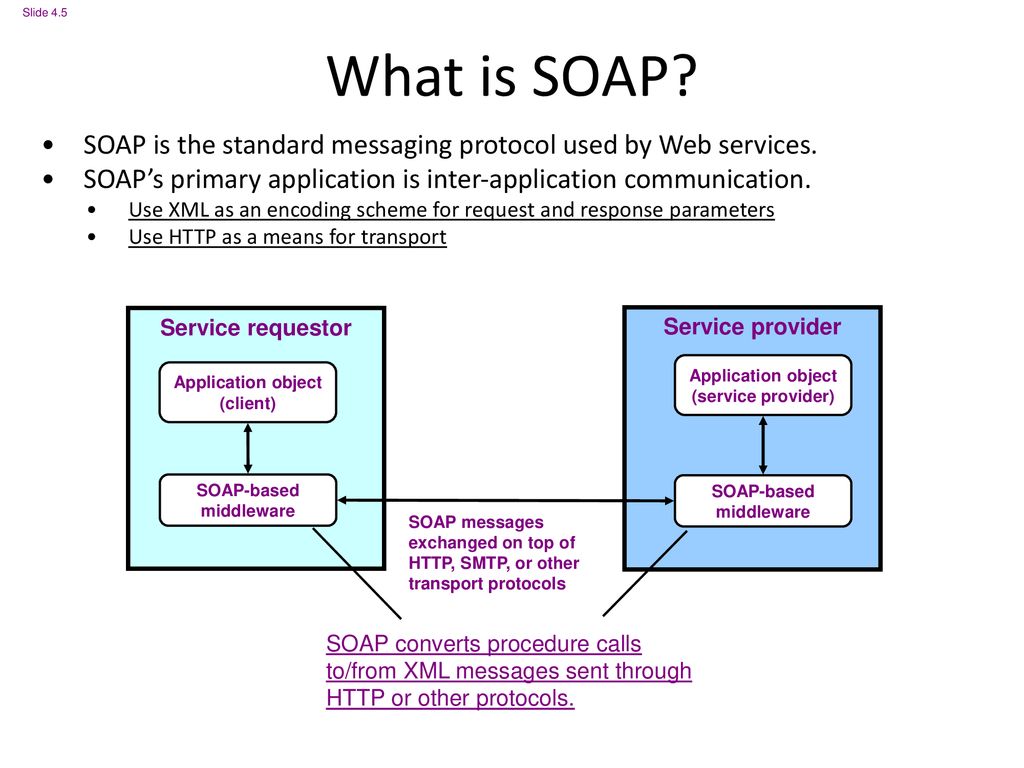
SOAP (Simple Object Access Protocol) is an XML-based protocol for sending and receiving messages over the internet. It is typically used for building web services and is often used as an alternative to REST.
SOAP messages are typically sent over HTTP, but can also be sent over other transport protocols such as SMTP (Simple Mail Transfer Protocol). A SOAP message consists of an Envelope element, which contains a header and a body. The header contains metadata, such as authentication information, while the body contains the actual data being sent.
Messages in SOAP are encoded in XML specifically and have a properly defined format:
Envelope: Literally envelopes the entire message/data in tags.
Header: Defines all extra information that might be needed to process this data. This is an optional element.
Body: This is where we actually write the request for data required/ where all the requested data is added.
Fault: Defines all the errors that may arise in the data during/due to transmission and measures to handle them.
REST Protocol

REST protocols overcome SOAP's dependency on XML by including JSON (the most popular), HTML, Python, plain text, and media files, REST protocols get around SOAP's reliance on XML. However, REST eliminates SOAP's extensibility to other protocols by only using HTTP/HTTPS for data delivery. RESTful APIs are APIs that use the REST protocol.
Client-server architecture and statelessness are requirements for REST APIs. It is implied by stateless communication that no client data is kept in memory in between GET queries. All of these GET queries to need to be separate and unconnected. Every action in REST is given a distinct URL, allowing the server to know exactly what to do in response to a request by knowing which instructions to carry out. Caching is supported via REST. Thus, in order to increase speed and efficiency, the browser can locally store the results of the request and periodically retrieve them as needed.
A typical REST request has the following components:
Endpoint: The destination URL from which data is being requested.
Method: We use predefined methods such as GET, POST, PUT or DELETE to fetch the data. These methods vary from one another. Ex. when using GET, the data is appended to the end of the URL string, whereas in POST, the data is sent along with the HTTP request.
Headers: They define the request's details and dictate the proper format in which the response must be received.
Body: The actual data sent by the service.
What are the main types of HTTP vulnerability?

Cross-site scripting - Commonly known XSS is when an attacker injects HTML markup or JavaScript into the affected web application's front-end client.
SQL injection - SQL injection is a code injection technique that might destroy your database.
DDOS attacks - A distributed denial-of-service (DDoS) attack is a malicious attempt to disrupt the normal traffic of a targeted server, service or network by overwhelming traffic
Cross-site request forgery - Cross-Site Request Forgery (CSRF) is an attack that forces an end user to execute unwanted actions on a web application in which they’re currently authenticated
How to secure an API?
The first method of security is to use HTTPS on your site
The second method of security is to use Password hash you can apply some logic to hash the password
The third method of security is to add a password over every endpoint so that no one can access it
The fourth method of security is to add timestamps in API authentication adding timestamps to APIs can help you secure the API.
If you have reached this point and have honestly read every part of this blog.

Give Yourself a Pat on back and keep Learning about API.

